Vulnerability Assessment Services
The rise in the Internet penetration of industrial and business sectors has enabled companies to have a strong online presence. They can find potential customers for their goods and services, as well as source raw materials economically from any supplier located at any place.
Most people are benefited from the Internet, but it has also increased the risk of malicious intruders stealing personal data and money. Cyber criminals are constantly searching for vulnerabilities in the software, system, or network to steal the assets and confidential data of a targeted company.
To protect its data, a business enterprise must take the necessary measures to identify security threats and flaws and take appropriate action to fix them. With vulnerability assessment and penetration testing or VAPT services, you can identify and correct any security flaws.
Vulnerability includes a programming error, a flaw, or a systemic weakness used to hack into a system network or server.
VAPT enables you to evaluate the system components to identify the security defenses, as well as a vulnerability assessment of your system network or application. The first step in locating a bug or weak point in a system, network, or application is vulnerability assessment. On the other hand, penetration testing assists in locating the vulnerability.
You can get reliable vulnerability assessment services with the help of trustworthy technical experts, who produce excellent results. To find security flaws, you should be conversant with vulnerability assessment methodologies.
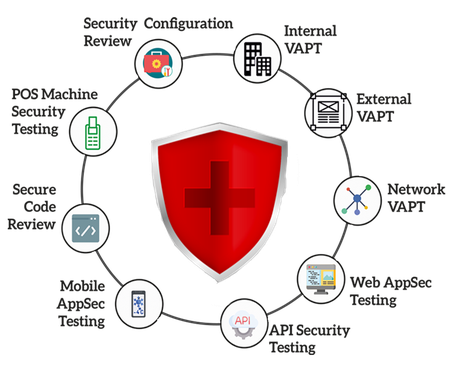
Know What Do Vulnerability Assessment Services include
Since hackers use a variety of tools, techniques, and strategies to penetrate security systems and networks, a business enterprise should routinely check its cyber security. By performing VAPT testing, you can get a comprehensive evaluation of your system application, a careful analysis of the threats, and suggestions on how to handle them.
Your online store or company can comply with the necessary industrial security standards for GDPR assessment, PCI DSS certification, ISO 27001, or HIPAA assessment. You can have managed services and system components regularly scanned for vulnerabilities to identify and eliminate false positives by partnering with a reputable VAPT service provider, who can offer you the VAPT services for:
• System Infrastructure
Network: Reliable vulnerability assessment services will check your network security’s potency in network access limitation, network segmentation, firewall implementation, and remote connectivity.
Email: They also check your email accounts’ susceptibility to phishing and spam.
• Applications
Web applications: Any security flaws in web applications, as well as their source code, are detected using front-end automated vulnerability scanning tools or static/dynamic source code analysis.
Mobile application: Various mobile application scanning tools are used to check for any security gaps or weaknesses in a mobile app.
Desktop application: To determine how data is distributed and maintained, it is evaluated.
You should ensure that your business hires the best vulnerability assessment services from a leading provider if you want to protect your business’ confidential data.